| |
|
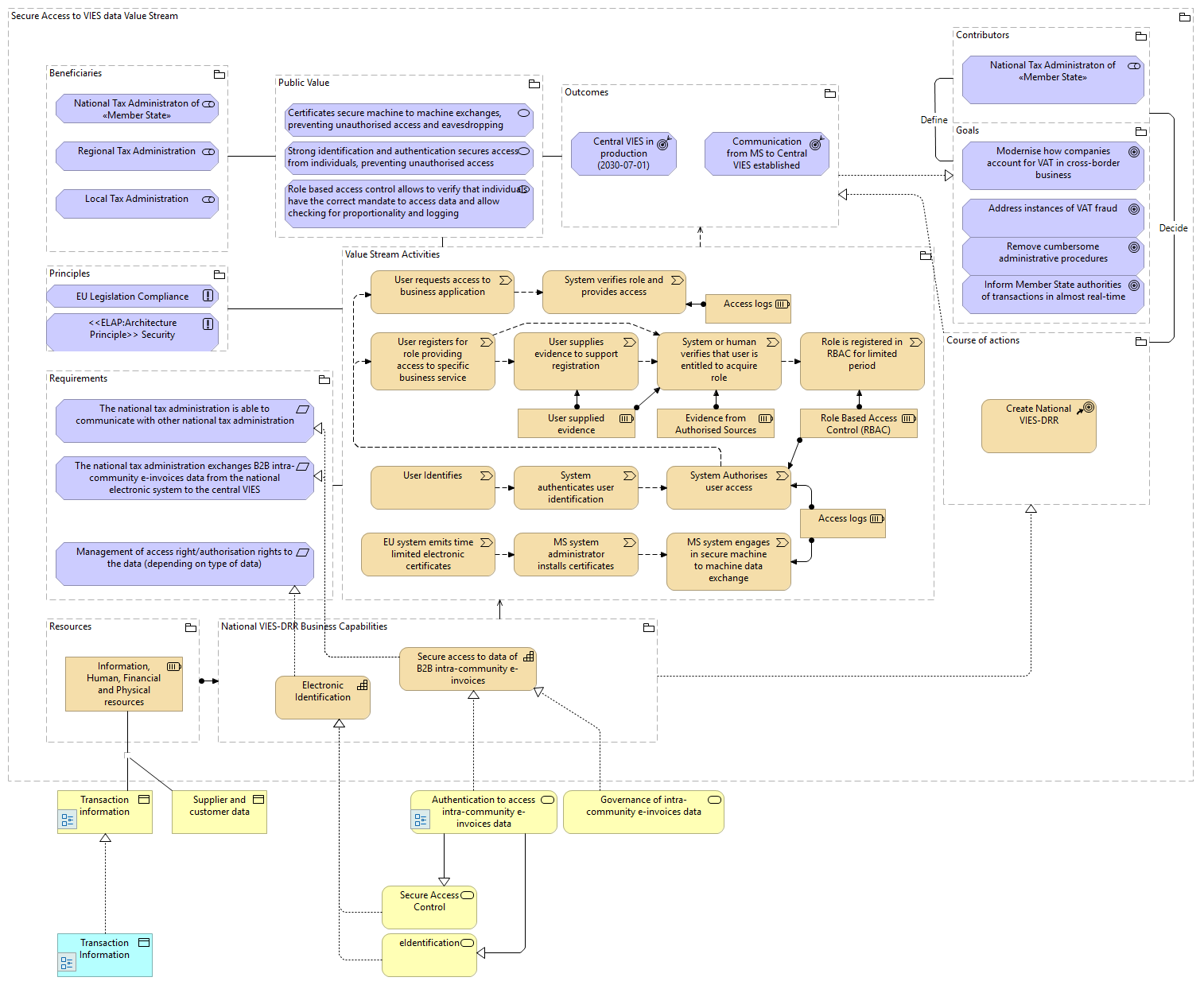
Secure Access to VIES data Value Stream |
Goals |
| |
|
Secure Access to VIES data Value Stream |
Course of actions |
| |
|
Secure Access to VIES data Value Stream |
Value Stream Activities |
| |
|
Secure Access to VIES data Value Stream |
National VIES-DRR Business Capabilities |
| |
|
Secure Access to VIES data Value Stream |
Contributors |
| |
|
Secure Access to VIES data Value Stream |
Resources |
| |
|
Secure Access to VIES data Value Stream |
Principles |
| |
|
Secure Access to VIES data Value Stream |
Requirements |
| |
|
Secure Access to VIES data Value Stream |
Public Value |
| |
|
Secure Access to VIES data Value Stream |
Outcomes |
| |
|
Secure Access to VIES data Value Stream |
Beneficiaries |
| |
|
Requirements |
Value Stream Activities |
| |
|
Requirements |
Management of access right/authorisation rights to the data (depending on type of data) |
| |
|
Requirements |
The national tax administration exchanges B2B intra-community e-invoices data from the national electronic system to the central VIES |
| |
|
Requirements |
The national tax administration is able to communicate with other national tax administration |
| |
|
Principles |
Value Stream Activities |
| |
|
Principles |
EU Legislation Compliance |
| |
|
Principles |
<<ELAP:Architecture Principle>> Security |
| |
|
Resources |
National VIES-DRR Business Capabilities |
| |
|
Resources |
Information, Human, Financial and Physical resources |
| |
|
National VIES-DRR Business Capabilities |
Course of actions |
| |
|
National VIES-DRR Business Capabilities |
Value Stream Activities |
| |
|
National VIES-DRR Business Capabilities |
Secure access to data of B2B intra-community e-invoices |
| |
|
National VIES-DRR Business Capabilities |
Electronic Identification |
| |
|
Secure access to data of B2B intra-community e-invoices |
The national tax administration is able to communicate with other national tax administration |
| |
|
Secure access to data of B2B intra-community e-invoices |
The national tax administration exchanges B2B intra-community e-invoices data from the national electronic system to the central VIES |
| |
|
Electronic Identification |
Management of access right/authorisation rights to the data (depending on type of data) |
| |
|
Value Stream Activities |
Outcomes |
| |
|
Value Stream Activities |
Public Value |
| |
|
Value Stream Activities |
User Identifies |
| |
|
Value Stream Activities |
System authenticates user identification |
| |
|
Value Stream Activities |
System Authorises user access |
| |
|
Value Stream Activities |
User registers for role providing access to specific business service |
| |
|
Value Stream Activities |
System or human verifies that user is entitled to acquire role |
| |
|
Value Stream Activities |
User supplies evidence to support registration |
| |
|
Value Stream Activities |
Role is registered in RBAC for limited period |
| |
|
Value Stream Activities |
User supplied evidence |
| |
|
Value Stream Activities |
Evidence from Authorised Sources |
| |
|
Value Stream Activities |
Role Based Access Control (RBAC) data |
| |
|
Value Stream Activities |
User requests access to business application |
| |
|
Value Stream Activities |
System verifies role and provides access |
| |
|
Value Stream Activities |
EU system emits time limited electronic certificates |
| |
|
Value Stream Activities |
MS system administrator installs certificates on MS systems |
| |
|
Value Stream Activities |
MS system engages in secure machine to machine data exchange |
| |
|
Value Stream Activities |
Access logs |
| |
|
Value Stream Activities |
Access logs |
| |
|
User Identifies |
System authenticates user identification |
| |
|
System authenticates user identification |
System Authorises user access |
| |
|
System Authorises user access |
User registers for role providing access to specific business service |
| |
|
System Authorises user access |
User requests access to business application |
| |
|
User registers for role providing access to specific business service |
User supplies evidence to support registration |
| |
|
User registers for role providing access to specific business service |
System or human verifies that user is entitled to acquire role |
| |
|
System or human verifies that user is entitled to acquire role |
Role is registered in RBAC for limited period |
| |
|
User supplies evidence to support registration |
System or human verifies that user is entitled to acquire role |
| |
|
User supplied evidence |
User supplies evidence to support registration |
| |
|
User supplied evidence |
System or human verifies that user is entitled to acquire role |
| |
|
Evidence from Authorised Sources |
System or human verifies that user is entitled to acquire role |
| |
|
Role Based Access Control (RBAC) data |
Role is registered in RBAC for limited period |
| |
|
Role Based Access Control (RBAC) data |
System Authorises user access |
| |
|
User requests access to business application |
System verifies role and provides access |
| |
|
EU system emits time limited electronic certificates |
MS system administrator installs certificates on MS systems |
| |
|
MS system administrator installs certificates on MS systems |
MS system engages in secure machine to machine data exchange |
| |
|
Access logs |
System Authorises user access |
| |
|
Access logs |
MS system engages in secure machine to machine data exchange |
| |
|
Access logs |
System verifies role and provides access |
| |
|
Public Value |
Outcomes |
| |
|
Public Value |
Certificates secure machine to machine exchanges, preventing unauthorised access and eavesdropping |
| |
|
Public Value |
Strong identification and authentication secures access from individuals, preventing unauthorised access |
| |
|
Public Value |
Role based access control allows to verify that individuals have the correct mandate to access data and allow checking for proportionality and logging |
| |
|
Beneficiaries |
Public Value |
| |
|
Beneficiaries |
National Tax Administraton of «Member State» |
| |
|
Outcomes |
Goals |
| |
|
Outcomes |
Communication from MS to Central VIES established |
| |
|
Outcomes |
Central VIES in production (2030-07-01) |
| Decide |
|
Contributors |
Course of actions |
| Define |
|
Contributors |
Goals |
| |
|
Contributors |
National Tax Administraton of «Member State» |
| |
|
Goals |
Inform Member State authorities of transactions in almost real-time |
| |
|
Goals |
Remove cumbersome administrative procedures |
| |
|
Goals |
Address instances of VAT fraud |
| |
|
Goals |
Modernise how companies account for VAT in cross-border business |
| |
|
Course of actions |
Outcomes |
| |
|
Course of actions |
Create National VIES-DRR |
| |
|
Transaction Information |
Transaction information |
| |
|
Governance of intra-community e-invoices data |
Secure access to data of B2B intra-community e-invoices |
| |
|
Authentication to access intra-community e-invoices data |
Secure Access Control |
| |
|
Authentication to access intra-community e-invoices data |
Secure access to data of B2B intra-community e-invoices |
| |
|
Authentication to access intra-community e-invoices data |
eIdentification |
| |
|
Secure Access Control |
Electronic Identification |
| |
|
eIdentification |
Electronic Identification |